Social engineering is a term that often gets thrown around in conversations about cybersecurity. But what does it really mean? At its core, social engineering exploits human psychology to manipulate individuals into divulging confidential information or performing actions that compromise security. It’s not just about high-tech hacks; it’s about understanding how people think and behave.
As the digital landscape evolves, so do the tactics used by malicious actors. These strategies can be subtle yet highly effective, catching even the most vigilant among us off guard. Whether it’s through phishing emails, phone scams, or deceptive messages on social media, recognizing these tactics becomes crucial in protecting ourselves and our personal information.
In this post, we will explore various aspects of social engineering—breaking down common tactics employed by attackers, examining real-life examples that highlight its dangers, and offering practical tips to bolster your defenses against such threats. Let’s dive into the world of social engineering and learn how to recognize these deceptive practices before they lead us astray.
Understanding Social Engineering

Social engineering is the art of manipulating people into giving up sensitive information. Unlike traditional hacking, it relies on psychological tricks rather than technical skills.
At its core, social engineering targets human emotions—fear, trust, curiosity. Attackers study their victims to exploit vulnerabilities in judgment and decision-making.
These tactics can be incredibly effective because they don’t require advanced technology. A simple phone call or email can lead to significant breaches if someone is not cautious.
Understanding the motivations behind these attacks is vital. Criminals often aim for quick gains by preying on urgency or authority figures in organizations.
Awareness plays a crucial role in recognizing when something feels off. The more we learn about how social engineers operate, the better equipped we become to resist their manipulations.
Common Tactics Used in Social Engineering
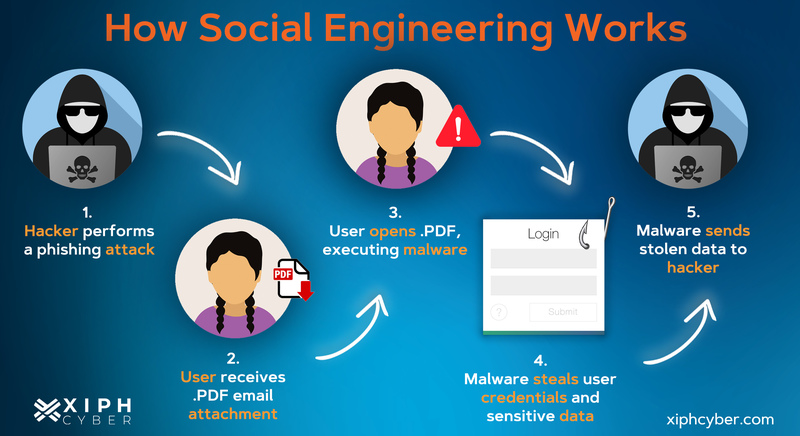
Social engineering exploits human psychology to manipulate individuals into divulging sensitive information. One common tactic is phishing, where attackers send deceptive emails that appear legitimate. These messages often urge recipients to click on malicious links or provide personal data.
Another tactic is pretexting. Here, the attacker creates a fabricated scenario to obtain information from the target. This could involve posing as a trusted figure like a bank representative or IT personnel.
Baiting involves enticing targets with something appealing—free downloads or prizes—to lure them into compromising situations. The promise of rewards can cloud judgment and lead to dangerous clicks.
Tailgating takes advantage of physical security breaches by following authorized personnel into restricted areas. It highlights how social cues can be just as crucial as technical barriers in safeguarding sensitive environments.
The Role of Technology in Social Engineering

Technology plays a pivotal role in social engineering. It acts as both a tool and an enabler for attackers.
Hackers leverage cutting-edge technology to manipulate individuals into revealing sensitive information. Phishing emails, often disguised as legitimate communications, are prime examples of this tactic. These emails exploit trust and urgency to prompt quick actions from unsuspecting victims.
Social media platforms also contribute significantly. They provide vast amounts of personal data that can be used for tailored attacks. A simple glance at someone’s profile can reveal enough details to craft compelling messages designed to deceive.
Moreover, advancements in AI have made it easier for fraudsters to automate their schemes. Chatbots mimic human conversation convincingly, allowing scammers to engage potential targets without much effort.
As technology evolves, so do the strategies employed by social engineers. Staying informed about these developments is crucial for safeguarding personal information against such threats.
Real-Life Examples of Social Engineering

One notable case involved a hacker posing as an IT technician. They called employees at a large corporation, claiming to perform urgent system updates. Many unsuspecting workers provided their login credentials over the phone, leading to significant data breaches.
Another incident featured a targeted phishing email that appeared to come from a trusted bank. Recipients were lured into clicking on links that directed them to counterfeit websites. This resulted in stolen personal information and financial loss.
Social engineering isn’t just about tech-savvy criminals; sometimes it involves old-fashioned deception. A well-known scammer used fake identities and charisma at social gatherings to gain access to sensitive company information.
These examples highlight how easily manipulation can occur through trust and urgency, making awareness essential for everyone in today’s digital landscape. Each story serves as a reminder of the importance of vigilance against such tactics.
How to Protect Yourself Against Social Engineering
To shield yourself from social engineering, start by being skeptical. Question unexpected requests for sensitive information. If something feels off, trust your instincts.
Next, verify identities before sharing any data. Use official contact methods to confirm whether a request is legitimate or fraudulent.
Regularly update your passwords and use two-factor authentication wherever possible. This adds an extra layer of protection against unauthorized access.
Educate yourself about common tactics used in scams. The more you know, the less likely you’ll fall victim to manipulation.
Be cautious with personal information on social media. Cybercriminals often piece together details to craft convincing attacks.
Encourage open communication in your workplace or community about potential threats. Sharing experiences can help everyone stay alert and informed.
Educating Others on Recognizing and Preventing Social Engineering Attacks
Education is the first line of defense against social engineering attacks. Sharing knowledge with friends, family, and colleagues creates a more aware community.
Organize workshops or informal gatherings focused on cybersecurity awareness. Use real-life scenarios to illustrate potential risks and tactics employed by attackers.
Encourage open discussions about suspicious emails or calls. Creating an environment where people feel comfortable sharing their experiences can help identify patterns in social engineering methods.
Utilize digital resources like online courses and articles that focus on recognizing these threats. Share engaging materials that simplify complex topics related to cybersecurity.
Promote critical thinking skills among peers when evaluating unexpected requests for sensitive information. Empower others to ask questions before taking action, fostering a culture of caution and vigilance in detecting possible scams.
Conclusion
Recognizing social engineering tactics is crucial in today’s digital landscape. The methods employed by attackers are constantly evolving, making it essential to stay informed. Understanding the various strategies can make all the difference in protecting yourself and your organization.
Awareness is your first line of defense. By familiarizing yourself with common tactics like phishing, pretexting, or baiting, you equip yourself to spot red flags early on. Remember that social engineers often manipulate emotions—like urgency or fear—to exploit their targets.
Technology plays a dual role here. While some tools can help identify threats and protect against breaches, technology itself also provides new avenues for these malicious attacks. Cybersecurity measures such as firewalls and encryption offer protection but must be complemented with human vigilance.
Real-life cases illustrate just how impactful social engineering can be. From high-profile data breaches to personal identity theft stories, these incidents serve as reminders of what’s at stake if we let our guard down.
Protecting oneself involves not only being aware but actively engaging in preventive practices—like regularly updating passwords and verifying requests before sharing sensitive information. Take time to educate those around you; a well-informed community stands stronger against threats than individuals acting alone.
Staying one step ahead requires constant effort and awareness about recognizing social engineering tactics effectively while fostering an environment where everyone feels empowered to contribute to secu






